
The large attack causing intermittent outages across the web today highlights a crucial point of the internet structure that often goes unconsidered outside of IT circles. Often the easiest way to restrict access to a website is not to take down the website itself, but to cut off the figurative roads and junctions that connect it to end users. That often means compromising the DNS (domain name system) servers, spread throughout the world, that redirect traffic to the right location.
The DNS is a sort of all-encompassing directory of domain names. A domain, if you didn’t already know, is the string you type in to get to an internet destination — google.com, darkwebdrugs.onion, dabiqmagazine.edu. But computers don’t actually use that string to talk to each other. Every domain corresponds to a numerical IP address. So the DNS translates that text into numbers.
How DNS Works
Let’s say you want to go to selectall.com. In brief, the process goes something like this …
You type that URL in and hit enter. Your computer will then check its local DNS cache. If you’ve visited selectall.com before, the computer already knows the IP address to connect to and the process ends.
If not, it then asks the recursive nameserver of your internet service provider, a larger database of domains and corresponding IP addresses than the one on your computer. If your ISP doesn’t know, it asks the DNS root server, which analyzes the request for its top-level domain (e.g., .com, .net, and so on). For selectall.com, we then get sent to the .COM root server, which checks its records and directs to the domain’s nameserver, which finally gives you the IP address — the static, numerical network address where the servers hosting Select All live.
Managing this sort of domain system and making sure nameservers are globally accessible is a big industry. Large companies like Twitter pay someone else to worry about it, and Dyn is a large player in that field. Their Managed DNS service is what was hit by the DDoS attack today.
Here’s the thing about Dyn’s Anycast network: As large and stable as it almost always is, it is composed of just 18 servers around the world.
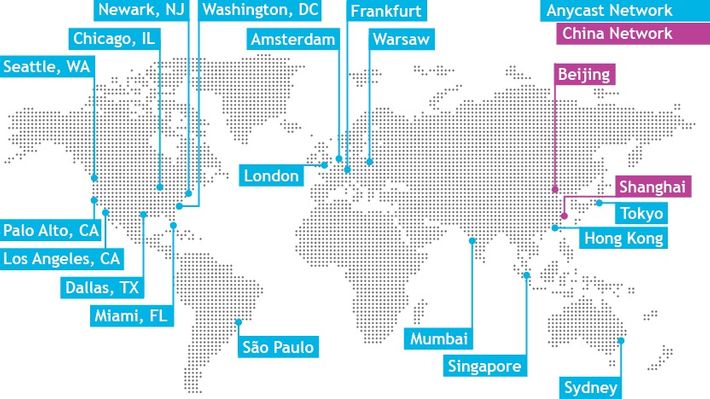
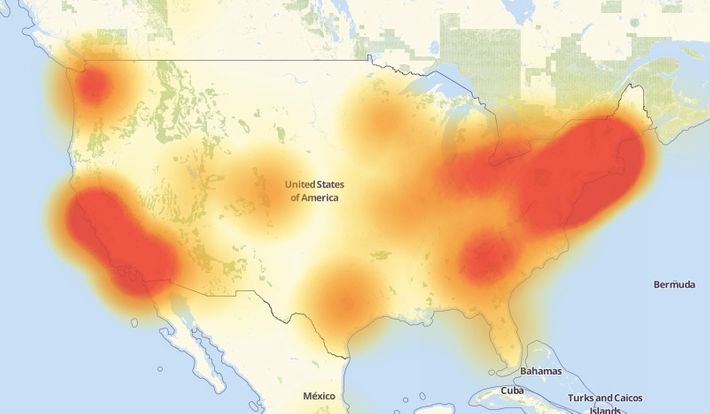
If you compare Dyn’s map with the heatmap of outages in the United States, you can see an obvious correlation.
How DDoS Works
So, how do you bring down a DNS server? First, you locate the server’s IP address, which shouldn’t be too tough to do, given how large a company Dyn is. Then, in today’s case, you launch a distributed denial-of-service (DDoS) attack.
Put simply, a DDoS attack hurls so much incoming traffic at a server that the server shuts down. There are many tools that can force this, but the best-known is the LOIC, or Low Orbit Ion Cannon, an open-source network stress-testing application.
But for most large infrastructures, one person with a LOIC won’t do the trick. That’s where botnets come in. Botnets are large groups of computers infected with malware, secretly, that can then be controlled remotely. So if you get a botnet of thousands of computers, each running a LOIC, you can overwhelm a server’s bandwidth.
In short, focus a tsunami of data packets at one of Dyn’s dozen and a half pressure points, and you get the outages currently being experienced around the U.S. Add more and more devices that can be hijacked into the mix, and you’re providing more points of infiltration that prevent you from checking your Facebook.
What’s Next
A growing concern is that more and more devices with internet capability are being produced, gadgets that are known as the Internet of Things. Every Nest thermostat or Wi-Fi-enabled lightbulb offers another point of intrusion that can be used for cyberattacks. This isn’t hyperbole: Last month, a website was brought down by a botnet that included more than 145,000 cameras.
More internet-connected devices means more strain on the network. Are we in danger of the entire internet collapsing under the strain? Not really — Dyn is just one DNS services provider in a sea of them. But cybersecurity experts are warning that yet-unknown entities are stress-testing the system, so there’s a good chance that we will see more incidents like today’s in the near future.





























