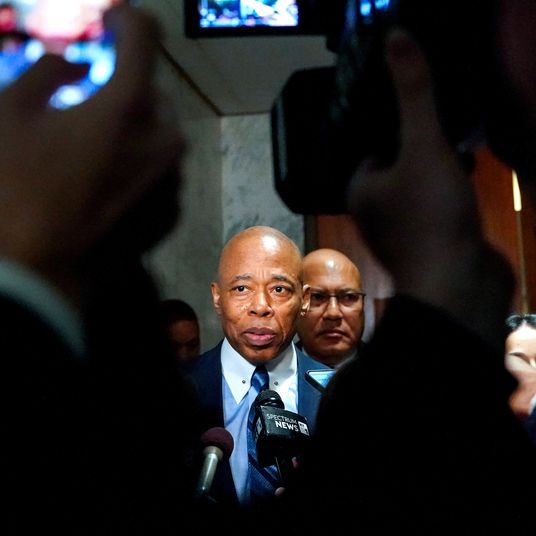On March 22, Apple and the FBI will meet in federal court to determine the fate of an iPhone: the 5s owned by San Bernardino shooter Syed Rizwan Farook. But what’s at stake is really the future of all iPhones — and maybe all phones in general.
The FBI is asking Apple to write software to break into a terrorist’s iPhone. Apple says that doing so would compromise every iPhone-owner’s security. Experts in fields from computer science to law enforcement to cryptography to trade-secret law are all increasingly worried about the implications of the government winning the case, which Apple has promised to take to the Supreme Court if necessary.
Based on conversations with experts, we’ve imagined a set of hypothetical future news stories (in italics) describing scenarios that could come to pass if the FBI wins, followed by explanations for why these stories are realistic.
FBI Comes Under Attack for Alleged Apple-Key Leak
As human rights groups across the globe amass evidence they claim demonstrates that Apple’s top-secret developer key has fallen into the hands of authoritarian governments and police forces, several sources inside the Federal Bureau of Investigation say the domestic law-enforcement agency has begun an internal review process to see whether the digital signature used by Apple to authenticate updates to its phones could have been leaked by FBI agents or contractors working on the phones. Apple has so far declined to comment, but privacy advocates and experts say that there is little oversight or accountability in the complex and multi-party process by which Apple “cracks” iPhones for law enforcement, and claim it is possible — if not likely — that the key was copied during one procedure and sold on the black market. Complicating the FBI’s investigation, sources say, is the fact that neither Apple nor the FBI know whether the key has actually been leaked.
The court order obtained by the FBI directs Apple to create an alternate version of iOS that would help agents circumvent the lock on the phone — a major component of Apple’s heightened encryption, which has been strongly criticized by the government for not leaving it an easy backdoor. The FBI can’t create this software itself because Apple, like all other major technology companies, code signs its software updates with a secret key that ensures other parties, like hackers or the government, can’t send you malware that looks like a legitimate software update. (For more on code-signing and other words, phrases, and concepts that might be confusing, see our Apple vs. FBI glossary.)
According to Steven Bellovin, co-director of the Cybersecurity and Privacy Center at Columbia University’s Data Science Institute, and one of the creators of USENET, Apple can comply with that request in one of two ways: Create new software specific to that phone’s serial number (and handle each future case individually), or create a more general version. “Either has its drawbacks,” said Bellovin. “In the former case, there’s an issue of [the government] needing too much access to the signature mechanism” — attracting parties who want to subvert Apple’s signing process, or signers — “in the latter, [simply giving the government] the code is very risky because it can unlock many phones.”
The importance of signing — authenticating — the software can’t be overstated. The key used to sign software is likely under a megabyte, making it extremely easy to put onto a thumb drive, attach to an email, or share on social media. Additionally, Apple has no real way of knowing whether the key has gotten out. Likely what Apple uses to keep the key secret is something called a Hardware Security Module (HSM), which puts the process of signing software through even more encryption and requires multiple people to access the key. HSMs are difficult to use and are expensive, even more so when you factor in the additional human labor.
Currently, Apple only signs a few software updates a year, making HSMs and their protection a relative non-issue. But if law enforcement agencies are making regular requests, Apple would likely need to set up a dedicated in-house infrastructure for cracking phones — what Matthew Green, an assistant professor at Johns Hopkins University’s Information Security Institute, calls “a factory for unlocking phones.” Once a significant number of people and resources are assigned to accessing iPhones for law enforcement, Green says, “that’s when risk gets really high of the software getting out.”
Since the act of creating the software to bypass the phone’s encryption will, by definition, make iPhones more vulnerable, according to MIT technologist Jeffrey Schiller, it constitutes a backdoor for the government. “In general, [backdoors require] more complex mechanisms to implement then security systems that do not provide for it,” Schiller wrote on his blog. “Complex systems fail in complex ways. Complex systems by their very nature are less secure because it is harder to reason about their security properties.”
Apple Access Requests Appear to Target Political Activists
A months-long investigation into device-access requests made by the city’s police department to Apple and other technology companies has found a disproportionate number of political activists and groups among the targets. Though most of the department’s requests concerned investigations into drug trafficking or gang activity, a significant number concerned civil rights groups, anti-police brutality activists, and, in one case, a local politician and well-known police critic. The access requests are often used to target phones taken into evidence following arrest, and because of their wide berth allow police access to nearly every aspect of a phone, including its messages. The increasing reliance on technology companies to break into their own products is reflected across the country: Technology companies say they field thousands of device-access requests from law enforcement agencies at every level — local, state, and federal — every year, and even more that they cannot legally acknowledge or discuss.
Now that Apple has created its iPhone-unlocking factory, who will its customers be? On the domestic front, it’s helpful to look at other government surveillance. The StingRay phone-surveillance system was originally built for the military and spy agencies by the Harris Corporation. Designed to mimic cell towers, StingRays trick cell phones into transmitting the location and identifying information of the owner, as well as those who happen to be physically near them. Documents obtained by the ACLU of Northern California also showed that StingRays can bug and record phone conversations. Also known as Triggerfish, among other things, they’ve been in regular use by federal law enforcement since at least the mid-1990s. Over the past decade and a half, though, their use has spread to state and local law enforcement organizations in nearly half of America, largely thanks to grants from the Department of Homeland Security.
Here are a few ways that local law enforcement used their new toys:
● Chicago police regularly use StingRays to monitor protesters and activists
● Baltimore police found a cell-phone thief
● A full third of StingRay uses by Tallahassee police between 2007 and 2014 were for property crimes
● Miami police made an emergency purchase of StingRays specifically to monitor protesters outside the Free Trade Area of the Americas Conference in 2003
Most experts I spoke with saw a similar path for encrypted-device access. “There is definitely the possibility of this sort of demand becoming abused in the same nature as StingRays have, particularly if the government begins demanding that the company receiving the order remain silent about the fact that they have received it, as they so often do,” said Ross Schulman, senior policy counsel at the New America Foundation’s Open Technology Institute, referring to the fact that both the Harris Corporation and the federal government often force local law enforcement agencies to sign non-disclosure agreements upon receiving surveillance equipment.
“Everything starts out as an exclusive tool,” said Jonathan Zdziarski, an iOS security expert. “These tools are the same tools I’ve written myself on older iPhones. The tool they’re requesting exists because I wrote it. My tools went from being used in terrorist cases, fast forward, cops are using it to jailbreak their girlfriend’s phones .… We’ve already seen this play out.”
That path of military to federal law enforcement to local police forces brings opportunities for civil liberties- and privacy violations, increasing more and more as smaller and smaller agencies get their hands on them. “If they have that tool, they’re gonna use it,” said Stephen Downing, a former deputy chief with the LAPD and a speaker for Law Enforcement Against Prohibition, who took care to note that he didn’t firmly fall on either side of the issue. “Some, like with all else, will abuse it. We’ve clearly seen abuses across the country at the federal level and at the local level, so if they had that capability, it’s gonna be used.”
“The thing that nobody’s talking about is messaging,” said Green. “If you look at FBI statements over last year, they talk about phone decryption and they talk about messaging services, how they can’t decrypt messages. What is not being discussed is the implications of if the FBI uses this to go after messaging systems.”
It’s not hard to see a future in which, according to Chris Soghoian, principal technologist at the ACLU, the government writes its own software to spy on Americans using their own devices, then has a judge sign a court order, and sends it off to Apple’s phone-unlocking factory. Previously, if the government wanted to record what was going on inside our homes, they had to break in and mic the place themselves. “We’ve brought the microphones into our homes,” said Soghoian.
The implications specifically for the War on Drugs are striking. According to the U.S. Court System’s 2014 Wiretap Report, 89 percent of all applications for phone wiretaps by law enforcement agencies were for drug cases. Anonymous government officials have been making overtures toward using a favorable ruling against “drug traffickers” in the media. “We know that drug dealers store evidence on devices, like inventory, and that dealers take photos of drug stashes, which sometimes include geotags,” said Zdziarski. “I can see typical law enforcement rifling through phones to see what’s interesting.” Downing said, “As you increase the scale, you increase the opportunity for abuse. The less oversight, the more abuse, basically, that’s been our experience.”
Apple Faces Familiar Fight, This Time in China
Apple and an intransigent government are entering a showdown over “backdoor” access to locked devices. Sound familiar? Think again: This time, it’s China. According to sources at Apple, speaking anonymously due to the sensitivity of the subject, after several weeks of pressure and legal maneuvering the Chinese government has essentially given Apple an ultimatum: Allow us access to locked iPhones, or close up shop in the country entirely. Where Apple might once have been able to avoid the problem by citing strict legal rules or political pressure in the U.S., the recent ruling upholding a judicial order forcing Apple to install a new version of its software on San Bernardino shooter Syed Rizwan Farook’s phone gives it less wiggle room. Adding to Apple’s woes is the fact that China represents about a quarter of Apple’s global sales — and its continued growth there is vital to its bottom line.
“The people I would worry about are foreign governments. People who have demonstrated they’re willing and able to hack U.S. security systems,” said Green. “The OPM hack” — in which Chinese hackers stole personal information about some 18 million government employees and contractors from the Office of Personnel Management from 2013 to 2015 — “was our Pearl Harbor.” Worth noting, too, are the at least three separate instances in recent years that Apple software has been targeted by groups originating in China, as well as FBI director James Comey’s 2014 claim, in an interview with 60 Minutes, that the Chinese government has hacked every major American company.
“It’s inevitable that the tools will end up in other people’s hands,” Zdziarski said. “We’re talking about every other government following in U.S. footsteps, ordering Apple to do what they want. It’s like ordering Apple to create an atomic bomb and then just putting a padlock on it.” Green agrees, saying that a ruling in the U.S. government’s favor would make it difficult for Apple to prevent other countries from compelling it — or other tech companies — to provide them with the software. “Once Apple announces they’re going to do this for the U.S. government, they’ll need to give that capability to China,” he said. And Apple certainly intends to keep operating in China, whose iPhone purchases surpassed America’s in April.
Elizabeth Rowe, director of the University of Florida’s Program in Intellectual Property Law, says that while there’s no direct international legal precedent that would be set by a U.S. court ruling in the U.S. government’s favor, “American courts are a world leader. If a court in China says Apple should do this, the fact that American courts allow this would hurt Apple in a Chinese court. It would be hard to say with a straight face that Apple can comply with America and not with China. Once the floodgates are open, they’re kind of open all over.”
The vulnerabilities being exploited by private, or non-governmental, interests is a concern, too. “The fact is that this software will absolutely become a target,” said Schulman. “Apple is good at security, but against a truly determined opponent it is hard to be sure that any kind of security is enough. The mere existence of the software the FBI is demanding is a danger.” Additionally, the software the FBI is requesting constitutes a trade secret, according to Rowe, “and they sure as heck do not want to give that over to the FBI.” If the key were to get out, even if it ended up being the government’s fault, it would regardless cease to be a trade secret by definition, and susceptible to then-legal use by competitors.”